Modernizing device authentication for your enterprise with Keytalk is essential for securing sensitive information. Keytalk offers robust encryption and seamless integration to streamline the login process and enhance user experience. You'll boost productivity by reducing login friction and ensuring strong security measures, such as multi-factor authentication. Plus, Keytalk adapts to your existing systems and complies with industry regulations. There's much more to explore about how Keytalk can transform your authentication strategy effectively.
Key Takeaways
- Keytalk provides robust encryption protocols, enhancing data security and modernizing device authentication for enterprises. Seamlessly integrates with existing systems, ensuring minimal disruption during the modernization process. Supports multi-factor authentication and biometrics, significantly reducing unauthorized access risks. Streamlines user experience with single sign-on capabilities, increasing productivity and reducing login friction. Helps maintain compliance with industry regulations, safeguarding sensitive data and minimizing non-compliance risks.
The Importance of Device Authentication in Today's Digital Landscape
As businesses increasingly rely on digital technologies, the importance of device authentication can't be overstated. It’s your first line of defense against unauthorized access and data breaches.
By ensuring that only verified devices connect to your network, you mitigate risks that could compromise sensitive information. You need to recognize that every device poses a potential vulnerability; if it's not authenticated, it could be a gateway for cyber threats.
Ensuring only verified devices connect to your network reduces vulnerabilities and protects against potential cyber threats.
Additionally, robust device authentication enhances user trust, as employees and clients feel secure knowing their data is protected.
In today’s fast-paced digital landscape, implementing strong device authentication measures is essential for maintaining operational integrity and safeguarding your organization’s assets.
Don't underestimate its role in your overall security strategy.
Keytalk Overview: Features and Benefits
When you choose Keytalk for your device authentication needs, you're not just adopting a tool; you're investing in a thorough security solution.
Keytalk offers a range of features designed to enhance your organization's security posture. With its robust encryption protocols, you can trust that your device data remains secure.
The platform supports seamless integration with existing systems, allowing for a smooth shift without disrupting your operations. You'll appreciate the flexibility Keytalk provides, enabling you to manage various devices effortlessly.
Additionally, its scalability guarantees that as your organization grows, your authentication needs are met.
Simplifying User Experience With Keytalk
With Keytalk, you can streamline your login processes, making access to your enterprise resources faster and more efficient.
Enhanced security measures guarantee that your data stays protected while you enjoy seamless access across multiple devices.
This combination not only simplifies your user experience but also strengthens your organization’s security posture.
Streamlined Login Processes
Streamlined login processes are essential for enhancing user experience, especially in enterprise environments where efficiency is key.
With Keytalk, you can simplify the way users access their devices and applications, reducing the friction often associated with traditional authentication methods. Instead of juggling multiple passwords or remembering complex credentials, your team can enjoy a seamless login experience through single sign-on capabilities.
By integrating Keytalk’s solutions, you can eliminate unnecessary steps, allowing users to focus on their tasks rather than on logging in. This not only boosts productivity but also helps to foster a more positive work environment.
Ultimately, a streamlined login process saves time and enhances satisfaction, making it a vital aspect of modern enterprise operations.
Enhanced Security Measures
Enhanced security measures are essential for protecting sensitive information in enterprise environments, and Keytalk simplifies this process for you.
With its innovative approach, you can guarantee that your authentication methods are robust yet user-friendly.
Here are three key benefits of using Keytalk:
Strong Encryption: Your data gets encrypted at every level, making unauthorized access nearly impossible. User-Friendly Interface: Keytalk's intuitive design reduces the complexity of security protocols, guaranteeing that employees can easily navigate the system. Centralized Management: You can manage user access and security settings from a single platform, streamlining your administrative tasks.Seamless Multi-Device Access
As you juggle multiple devices in today’s fast-paced work environment, seamless access to your enterprise systems becomes essential. Keytalk streamlines the authentication process across all your devices, letting you focus on your tasks instead of struggling with logins.
With its intuitive interface, you can switch from your laptop to your tablet or smartphone without missing a beat. Keytalk’s single sign-on feature means you only enter your credentials once, simplifying your experience and saving you time.
Plus, robust security measures guarantee that your data remains protected, no matter which device you use. Embrace a smoother, more efficient workflow with Keytalk, and enjoy the freedom of accessing your enterprise systems effortlessly, wherever you are.
Enhancing Security Measures Against Cyber Threats
While the digital landscape continues to evolve, the threat of cyberattacks looms larger than ever, making robust security measures essential for enterprises.
You need to be proactive in safeguarding your organization against potential breaches. Here are three key strategies to enhance your security measures:
Implement Multi-Factor Authentication (MFA): This adds an extra layer of protection, ensuring that even if passwords are compromised, unauthorized access is still blocked. Regularly Update Software and Systems: Keeping your software current minimizes vulnerabilities that cybercriminals exploit. Conduct Routine Security Audits: Periodically evaluating your security posture helps identify weaknesses and improves your overall defense strategy.Integrating Keytalk With Existing Systems
Integrating Keytalk with your existing systems can greatly streamline your authentication processes, ensuring a seamless user experience.
You can effortlessly connect Keytalk to your current infrastructure—be it an on-premises solution or a cloud-based platform. Keytalk’s robust APIs allow for easy integration, enabling you to manage device identities without disrupting your workflows.
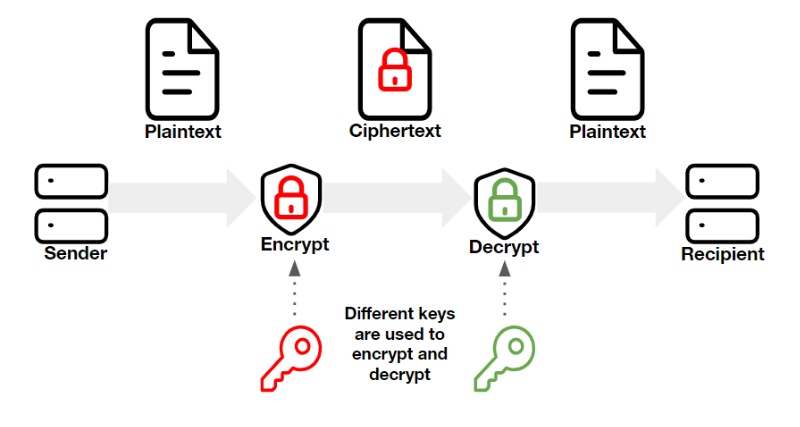
You'll also benefit from enhanced security features, like multi-factor authentication, which can be layered onto your existing systems. By utilizing Keytalk, you can centralize your authentication management, reducing administrative burdens and minimizing potential security vulnerabilities.
Enhance security with multi-factor authentication while centralizing management to reduce administrative burdens and vulnerabilities.
Plus, it supports various authentication protocols, making it flexible enough to fit into your unique requirements. Embrace this integration to modernize and fortify your enterprise’s authentication landscape.
Case Studies: Successful Implementations of Keytalk
 Secure Intent-based Search For Your Business
Secure Intent-based Search For Your BusinessIn this section, you’ll explore how Keytalk has transformed security protocols and streamlined authentication processes for various enterprises.
These case studies highlight real-world examples of successful implementations, showing you the tangible benefits of adopting Keytalk.
Let's look at how organizations have enhanced their security while simplifying user access.
Enhanced Security Protocols
As organizations face increasingly sophisticated cyber threats, implementing enhanced security protocols becomes essential for safeguarding sensitive data.
By leveraging Keytalk’s innovative solutions, you can greatly bolster your security framework. Here are three https://smalbizz.com/implementation-and-management-of-s-mime-certificates/ key enhancements to examine:
Multi-Factor Authentication (MFA): Integrating MFA adds an extra layer of security, ensuring that only authorized users gain access to sensitive information. End-to-End Encryption: Encrypting data at rest and in transit protects against unauthorized interception, making it much harder for attackers to access critical data. Continuous Monitoring: Implementing real-time monitoring allows you to detect anomalies and respond to potential threats proactively, minimizing the risk of breaches.Streamlined Authentication Processes
While many organizations struggle with cumbersome authentication processes, Keytalk’s solutions have successfully streamlined these systems, enhancing both user experience and security.
You can see this in various case studies showcasing how businesses transformed their authentication methods. For instance, a leading healthcare provider reduced login times by 75% after implementing Keytalk, allowing staff to focus more on patient care rather than access issues.
Another tech firm improved their security posture while speeding up the onboarding process for new employees.
By adopting Keytalk’s innovative approach, you can simplify authentication and eliminate frustrating barriers.
These real-world examples demonstrate that streamlined processes not only boost productivity but also maintain robust security standards, proving that efficiency and safety can go hand in hand.
Future-Proofing Your Authentication Strategy
To stay ahead in an ever-evolving digital landscape, businesses must proactively adapt their authentication strategies.
Future-proofing your approach is vital for maintaining security and user experience. Consider these three key areas:
Future-proofing your authentication strategy is essential for ensuring both security and a seamless user experience.
Embrace Multi-Factor Authentication (MFA): Implementing MFA considerably reduces the risk of unauthorized access by requiring multiple verification methods. Utilize Biometrics: Integrating biometric authentication can enhance security and streamline user access, making it harder for attackers to compromise accounts. Stay Informed on Trends: Regularly review advancements in authentication technologies and regulatory changes to guarantee your strategy remains relevant and compliant.Keytalk's Role in Regulatory Compliance
 Unlock Digital Identity Verification In The Cloud
Unlock Digital Identity Verification In The CloudStaying compliant with regulations is a challenge that many enterprises face, especially as authentication technologies evolve.
Keytalk simplifies this process by providing a robust framework that meets industry standards. With its advanced encryption and secure key management, you can guarantee sensitive data is protected and accessible only to authorized users.
Keytalk's solutions not only streamline user authentication but also help you maintain compliance with regulations like GDPR and HIPAA. By implementing Keytalk, you're not just enhancing security; you're also demonstrating your commitment to regulatory adherence.
This proactive approach minimizes risks associated with non-compliance, such as hefty fines and reputational damage. Embrace Keytalk to guarantee your authentication processes align with regulatory expectations while keeping your organization secure.
Getting Started With Keytalk for Your Organization
Getting started with Keytalk for your organization is easier than you might think, especially when you have a clear roadmap to follow.
Here’s how to kick off your journey:
Assess Your Needs: Identify your organization's unique authentication requirements and security challenges. This guarantees Keytalk aligns perfectly with your goals. Integrate Keytalk: Work with your IT team to seamlessly integrate Keytalk into your existing infrastructure.Utilize available documentation and support for a smooth shift.
Train Your Team: Provide training sessions for your staff to familiarize them with the new system.The more they know, the better they'll adapt and maximize Keytalk's capabilities.
Frequently Asked Questions
What Types of Devices Can Keytalk Authenticate?
Keytalk can authenticate a variety of devices, making it versatile for your needs. You’ll find it works with smartphones, tablets, laptops, and IoT devices.
Whether you’re using Android or iOS, Windows or macOS, you can rely on Keytalk to provide secure authentication. Its flexibility guarantees that you’re protected across different platforms.
How Does Keytalk Handle Lost or Stolen Devices?
When a device goes missing, it’s like losing a trusted companion.
Keytalk makes sure your data remains safe by allowing you to remotely revoke access to the device. You can easily initiate this process through your management portal, ensuring unauthorized users can’t access sensitive information.
Once you've reported the device as lost or stolen, Keytalk updates your security settings, keeping your enterprise secure and giving you peace of mind.
What Support Options Are Available for Keytalk Users?
When you’re looking for support options, you’ll find that Keytalk offers several resources to help you.
You can access their extensive documentation, which covers various topics and troubleshooting tips. If you need personalized assistance, their support team is available via email or phone, ready to address your concerns.
Additionally, you can participate in community forums where users share experiences and solutions, enhancing your overall experience with Keytalk’s services.
Can Keytalk Be Used in a Multi-Cloud Environment?
Yes, you can use Keytalk in a multi-cloud environment.
It’s designed to seamlessly integrate across various platforms, allowing you to manage authentication processes efficiently.
By leveraging its capabilities, you can maintain security and user access regardless of where your resources reside.
This flexibility helps you streamline operations and adapt to changing needs in your organization.
Just make sure you configure the settings correctly for peak performance across all cloud services.
How Does Keytalk Ensure Data Privacy for Users?
"Good fences make good neighbors." When it comes to data privacy, Keytalk takes this to heart.
It employs robust encryption methods to protect user information and guarantees secure communication channels.
You’ll find that it limits access to sensitive data, allowing only authorized users to interact with it.
With regular audits and compliance checks, Keytalk creates a trustworthy environment, giving you peace of mind about your data's safety and confidentiality.
Conclusion
In today’s rapidly evolving digital landscape, modernizing your device authentication with Keytalk is like upgrading from a rusty lock to a high-tech security system. By streamlining user experience, enhancing security, and ensuring compliance, you can safeguard your organization’s sensitive information. As cyber threats continue to grow, embracing Keytalk not only future-proofs your authentication strategy but also empowers your team. Don’t wait—take the leap and transform your authentication approach today!