Boosting X.509 authentication the smart way with Keytalk means simplifying certificate management while enhancing security. Keytalk’s automated processes cut down on manual workload, allowing you to focus on what really matters. You’ll benefit from streamlined access management and an improved user experience through Single Sign-On (SSO). With added features like Multi-Factor Authentication (MFA) and Certificate Pinning, you can protect sensitive data effectively. Find out how to further strengthen your security posture and optimize your authentication processes.
Key Takeaways
- Keytalk simplifies X.509 certificate management through automated processes, reducing manual workload for IT teams and enhancing efficiency. Streamlined Single Sign-On (SSO) allows users to access multiple applications with a single set of credentials, improving user experience. Multi-Factor Authentication (MFA) and Certificate Pinning enhance security measures, protecting against unauthorized access and man-in-the-middle attacks. Keytalk integrates seamlessly with existing systems, leveraging current infrastructure for cost-effective security enhancements without major overhauls. Future trends include AI integration and blockchain technology for improved security and dynamic validation in X.509 authentication processes.
Understanding X.509 Authentication
X.509 authentication is an essential standard in the domain of digital security, providing a framework for establishing trust between parties over networks.
X.509 authentication establishes a trusted framework for secure digital communications between networked parties.
You’ll find that X.509 certificates are digital documents that verify the identity of entities, ensuring secure communications. Each certificate contains a public key, issuer information, and validity dates, which you can use to authenticate a user or device.
When you connect to a secure website, your browser checks the X.509 certificate to confirm its legitimacy. If the certificate's valid, you can trust the connection.
This process relies on a hierarchy of trusted Certificate Authorities (CAs) that issue these certificates. Understanding how X.509 works empowers you to navigate digital spaces securely and confidently.
The Importance of Secure Online Identities
As you navigate the digital landscape, securing your online identity is more essential than ever.
Without proper protection, your personal information can easily fall into the wrong hands, leading to identity theft and fraud.
Here are three reasons why you should prioritize online security:
Data Protection: Safeguard sensitive information like passwords and financial details from cybercriminals.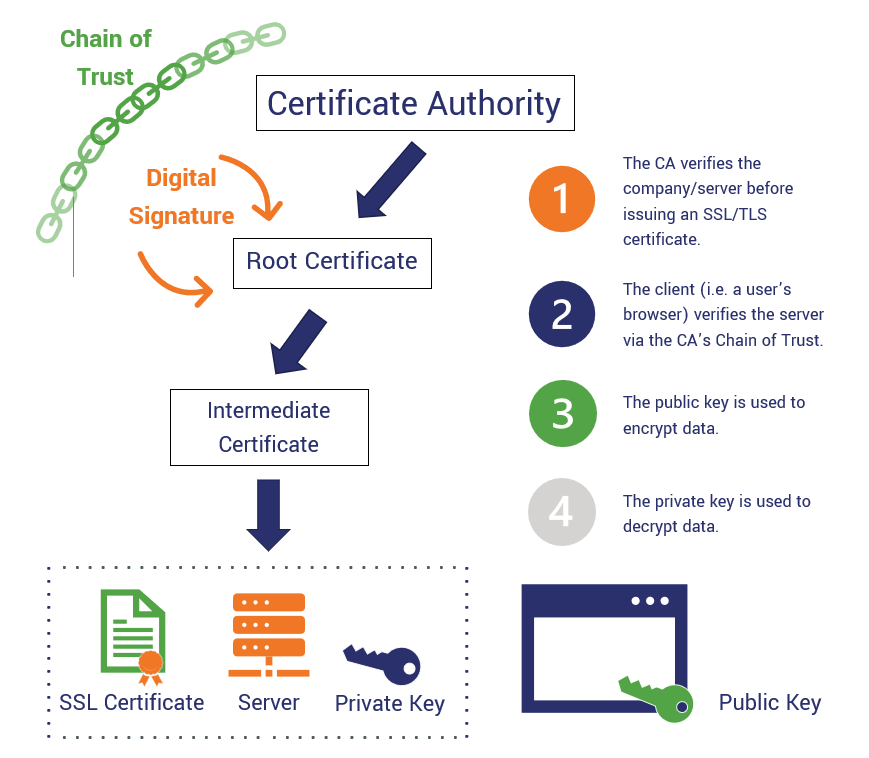 Control Vpn Access The Smart Way
Control Vpn Access The Smart WayKeytalk's Innovative Approach to X.509
When it comes to securing digital identities, Keytalk offers a groundbreaking approach to X.509 authentication that enhances both security and user experience.
You’ll appreciate how Keytalk leverages advanced technology to simplify certificate management, making it seamless to issue and renew certificates. This innovative method guarantees that you can authenticate users and devices with confidence, minimizing the risk of potential security breaches.
By integrating automated processes, Keytalk reduces the manual workload, allowing your IT team to focus on more critical tasks. Additionally, their solution supports a diverse range of devices and applications, ensuring compatibility across your organization.
Keytalk streamlines digital identity management, minimizing manual tasks and ensuring compatibility across diverse devices and applications.
With Keytalk, you’re not just improving security; you’re also streamlining your digital identity management for a more efficient and user-friendly experience.
Streamlining Authentication Processes
To guarantee a smooth user experience, streamlining authentication processes is essential in today’s fast-paced digital landscape. Simplifying these processes can greatly enhance user satisfaction and efficiency.
Here are three key strategies you can implement:
Single Sign-On (SSO): Allow users to access multiple applications with one set of credentials, reducing login fatigue and time spent on authentication. Automated Token Management: Use automation to manage tokens and certificates, minimizing manual tasks and decreasing the chance of human error. User-Friendly Interfaces: Design intuitive authentication interfaces that guide users seamlessly through the process, lowering frustration and improving engagement.Enhancing Security Measures With Keytalk
While traditional authentication methods provide a foundation for security, enhancing those measures with Keytalk can greatly bolster your defenses against unauthorized access.
Keytalk integrates advanced cryptographic techniques, ensuring your data remains protected. By leveraging automated certificate management, you can eliminate the risks associated with human error, considerably reducing vulnerabilities.
Moreover, Keytalk’s unique approach to identity verification allows you to implement multi-factor authentication seamlessly, making it harder for intruders to breach your systems.
You'll appreciate the real-time monitoring and alerts that keep you informed about any suspicious activities.
With Keytalk, you’re not just upgrading your authentication; you’re adopting a proactive security posture that adapts to evolving threats, ensuring your organization stays one step ahead of potential attackers.
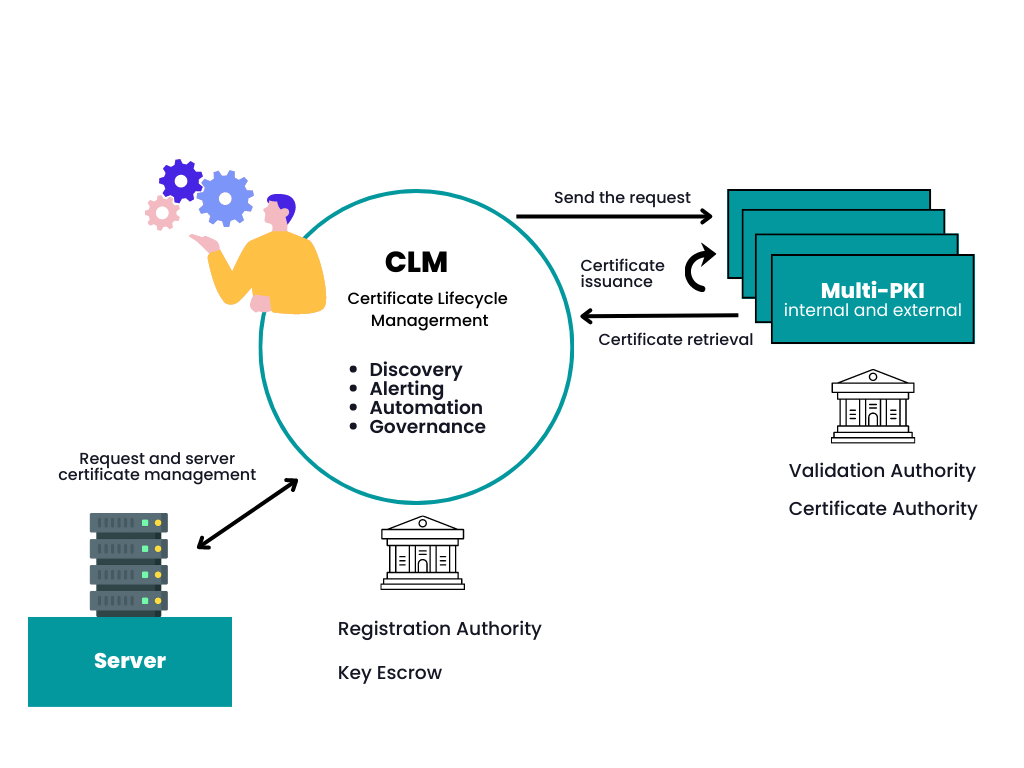
Integration With Existing Systems
When integrating X.509 authentication into your existing systems, you'll want to guarantee seamless compatibility.
A simplified deployment process can make the shift smoother, allowing you to focus on what matters most.
Custom integration solutions can also help tailor the system to your specific needs, enhancing overall efficiency.
Seamless System Compatibility
 Supercharge Device Authentication In 2025
Supercharge Device Authentication In 2025Integrating X.509 authentication into your existing systems can greatly streamline operations, especially as it enhances security protocols without major overhauls.
By focusing on seamless compatibility, you can enjoy numerous benefits:
Cost Efficiency: Leverage your current infrastructure, minimizing the need for expensive upgrades or replacements. User Experience: Maintain a familiar interface for your team, ensuring that onboarding remains smooth and hassle-free. Enhanced Security: Strengthen your security measures without disrupting daily operations, allowing you to safeguard sensitive data effectively.With these advantages, you can take full advantage of X.509 authentication, ensuring your systems are both robust and efficient.
Embracing this technology positions you to meet future challenges head-on while keeping your operations running smoothly.
Simplified Deployment Process
Deploying X.509 authentication can be a straightforward process, especially if you approach it with a clear strategy.
Start by evaluating your existing systems to identify where the integration will occur. You’ll want to guarantee that your current infrastructure supports X.509 certificates without major https://newscerr.com/certificate-lifecycle-management/ overhauls.
Utilize existing APIs and libraries to streamline the deployment, allowing you to leverage what you already have in place.
Testing is crucial, so create a plan to validate the integration before going live. Collaborate with your IT team to address any potential challenges early on.
Custom Integration Solutions
To guarantee a seamless integration of X.509 authentication with your existing systems, it’s essential to customize the solution to fit your unique environment. By doing so, you facilitate smoother operations and enhanced security.
Here are three key considerations for effective integration:
Compatibility: Assess your current systems and choose components that align well with X.509 standards to avoid disruptions. Scalability: Design the integration to accommodate future growth, facilitating that your authentication solution can evolve alongside your business needs. User Experience: Keep the end-user in mind; the integration should enhance usability without adding complexity or friction to their daily tasks.Real-World Applications and Success Stories
When you explore real-world applications of X.509 authentication, you’ll find enhanced security measures and streamlined access management at the forefront.
Many industries have successfully implemented these protocols, showcasing tangible benefits.
Let’s look at some compelling case studies that highlight these successes.
Enhanced Security Measures
As organizations increasingly rely on X.509 certificates for secure communications, enhanced security measures have become essential in real-world applications.
Implementing these measures not only fortifies your security posture but also instills trust among users. Here are three key enhancements that can make a difference:
Multi-Factor Authentication (MFA): By requiring multiple forms of verification, you greatly reduce the risk of unauthorized access. Certificate Pinning: This technique helps prevent man-in-the-middle attacks by guaranteeing that your application only accepts specific certificates. Automated Certificate Management: Streamlining the lifecycle of certificates minimizes human error and guarantees timely renewals, reducing vulnerabilities.Streamlined Access Management
While seamless access management can seem challenging, many organizations have successfully implemented X.509 certificates to simplify user authentication and enhance security.
By utilizing these certificates, you can streamline access for users, allowing them to authenticate quickly without compromising safety. For instance, companies often report reduced helpdesk calls related to password resets, as users can rely on their X.509 certificates for secure access.
This efficient process not only saves time but also boosts productivity across teams. Additionally, you’ll notice improved compliance with security regulations, as X.509 certificates provide robust identity verification.
As more organizations adopt this technology, you'll find yourself in good company, leveraging advanced solutions to meet modern access management demands effectively.
Industry-Specific Case Studies
Organizations in various industries are discovering the transformative power of X.509 certificates for enhancing security and streamlining operations.
Here are three compelling case studies showcasing their real-world impact:
Healthcare: A hospital utilized X.509 certificates to secure patient data and streamline electronic health record access, reducing unauthorized access incidents by 50%. Finance: A banking institution adopted X.509 authentication for secure transactions, leading to a 40% decrease in fraud-related losses within the first year. Manufacturing: A leading manufacturer implemented X.509 certificates for IoT devices, achieving seamless device authentication and enhancing overall system security.These success stories highlight how X.509 certificates can greatly bolster your organization’s security while improving efficiency across various sectors.
Future Trends in X.509 Authentication
Given the rapid evolution of technology, future trends in X.509 authentication are likely to involve enhanced security measures and greater automation.
You'll see a shift towards more dynamic validation processes, allowing certificates to adapt in real-time to emerging threats. Artificial intelligence could play an essential role, streamlining certificate management and reducing human error.
A shift towards dynamic validation processes will enable real-time adaptation of certificates to emerging threats, with AI enhancing management and reducing errors.
Expect to see integration with blockchain technology, which could provide a decentralized and tamper-proof method for verifying identities.
Additionally, as organizations adopt zero-trust architectures, X.509 authentication will become more vital in ensuring secure communications.
You'll need to stay informed about these developments to maintain a robust security posture, ensuring your systems remain resilient against evolving cyber threats.
Frequently Asked Questions
What Are the Costs Associated With Implementing Keytalk’S X.509 Solutions?
When considering the costs of implementing X.509 solutions, you’ll need to account for several factors.
These include initial setup fees, ongoing maintenance costs, and any required training for your team.
You might also face expenses related to hardware or software integration.
Additionally, think about potential costs for support services and updates.
How Does Keytalk Handle Customer Support for X.509 Authentication?
When you need assistance, you want quick responses, clear guidance, and reliable support.
Keytalk excels in all these areas for X.509 authentication. Their customer support team is available to answer your questions, troubleshoot issues, and provide in-depth solutions tailored to your needs.
You’ll find resources like documentation and FAQs on their website, ensuring you have the information you need at your fingertips.
With Keytalk, you’re never alone in your authentication journey.
Can Keytalk's Solution Be Customized for Specific Business Needs?
Yes, Keytalk's solution can definitely be customized to meet your specific business needs.
You can tailor the features and functionalities to align with your organization's requirements, ensuring you get the most out of the system.
What Training Resources Does Keytalk Offer for Users?
Keytalk offers a variety of training resources to help you maximize your use of their solutions.
You’ll find extensive documentation, video tutorials, and interactive webinars tailored to different skill levels. They also provide personalized training sessions, ensuring that you grasp the features that matter most to your organization.
Whether you’re new or experienced, these resources equip you with the knowledge needed to implement and manage your authentication effectively.
Does Keytalk Provide a Trial Period for Their X.509 Services?
Yes, Keytalk offers a trial period for their X.509 services, allowing you to explore its features before committing.
Did you know that over 70% of organizations report improved security after implementing strong authentication solutions?
With the trial, you can test the service’s capabilities and see how it enhances your security posture.
It’s a great opportunity to experience the benefits firsthand without any immediate financial commitment.
Conclusion
In the digital landscape, X.509 authentication is your shield against identity theft, guarding your online presence like a knight in shining armor. Keytalk’s innovative approach transforms this armor into a flexible, adaptive force, seamlessly integrating with your existing systems. As you venture into the future, embracing these advancements will let you navigate the online world with confidence, turning potential threats into mere shadows. Together, you can forge a path to secure identities and protect what matters most.